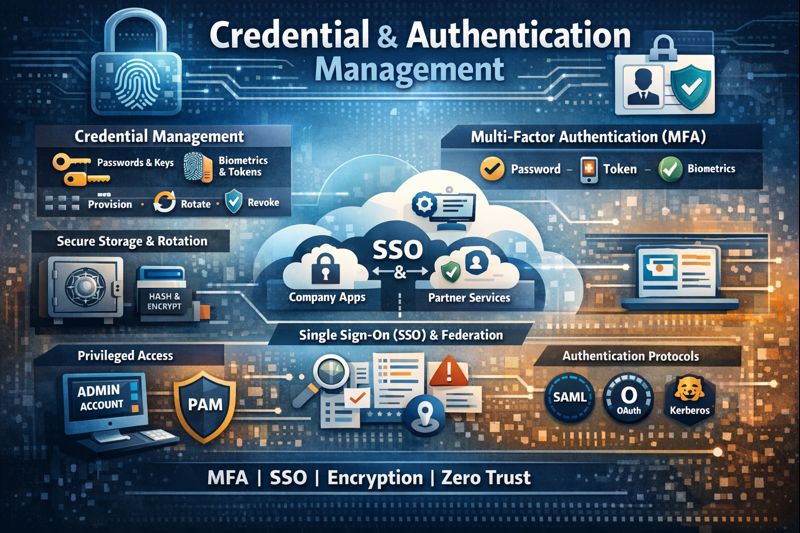
In Identity and Access Management (IAM), managing credentials and authentication means establishing controlled, auditable processes for issuing, protecting, validating, rotating, and revoking identity secrets while enforcing strong authentication mechanisms.
Credential Management
Credentials are proofs of identity. They are something you know, have, or are). Examples of credentials are passwords, passphrases, cryptographic keys, certificates, biometrics, and tokens.
Effective IAM manages credentials across the credential lifecycle management. The life cycle is as follows.
- Provisioning basically involves verifying identity before issuance and assigning credentials based on the principle of least privilege.
- Storage and Protection involves storing identity securely using processes such as strong hashing. Some form of credentials can be stored in secure vaults.
- Rotation and Expiration is when security policy such as password aging is enforced. Rotation of credentials such as cryptographic key can also be enforced. However, avoid forced rotation for low-risk users unless they are compromised
- Revocation and De-provisioning is when credentials are revoked or de-provisioned if a user leaves an organization or role changes or a compromise is suspected
It is advisable to set policies such as blocking credential reuse, using enterprise-approved password managers, and enforcing minimum password length over complexity.
Authentication Management
Authentication helps to validate credentials. With IAM, you can enforce one or more of the following for authentication management.
- Something you know e.g., Password
- Something you have e.g. Token
- Something you are e.g. Biometrics
- Somewhere you have e.g. Geolocation
Authentication can be implemented using different methods as follows
- Multi-Factor Authentication e.g., Password + Token/Biometric/App
- Passwordless Authentication
- Risk-Based Authentication
Authentication can be managed using centralized access Control and federation, privileged authentication controls, monitoring, logging, and auditing, and policy and government alignment.
For centralized access control, you can use, for example, Single Sign-On (SSO) process that allows authenticating once to have access to multiple systems. You can also set up controls to reduce password sprawl and phishing risk.
IAM credential and authentication management should align with the following standards.
- NIST SP 800-53 / 800-63
- ISO 27001
- Zero Trust Architecture
- Least Privilege & Separation of Duties
In summary, to manage credentials and authentication in IAM, you should
- securely issue, store, rotate, and revoke credentials
- enforce MFA and modern authentication protocols
- centralize authentication using SSO and federation
- apply stronger controls to privileged identities
- continuously monitor and audit authentication activity
and