Technology and its development has always been very interesting to me. One of the fields of technology that have taken keen interest is the security aspect. This field of technology is very important whether you are either a developer or a user of technology. It is also very important for anyone to know most of the key terms in technology security. This is because security starts with an understanding of what is to be secured.
One of such security terms in technology is Hashing. Hashing is generally defined as the process of using a mathematical algorithm against data to produce a numerical value that is representative of that data1, takes an input set of data (of almost arbitrary size) and returns a fixed-length result called the hash value. A hash function is the algorithm used to perform this transformation.
Hashes have many uses in computing and security, one of which is to create a message digest by applying such a hash function to the plaintext body of a message.
To be useful and secure, a cryptographic hash function must demonstrate five main properties:
- Useful
- Nonreversible
- Content integrity assurance
- Unique
- Deterministic
easy to compute the hash value for any given message.
computationally infeasible to reverse the hash process or otherwise derive the original plaintext of a message from its hash value (unlike an encryption process, for which there must be a corresponding decryption process).
computationally infeasible to modify a message such that re-applying the hash function will produce the original hash value.
computationally infeasible to find two or more different, sensible messages that hash to the same value.
same input will always generate the same hash, when using the same hashing algorithm.
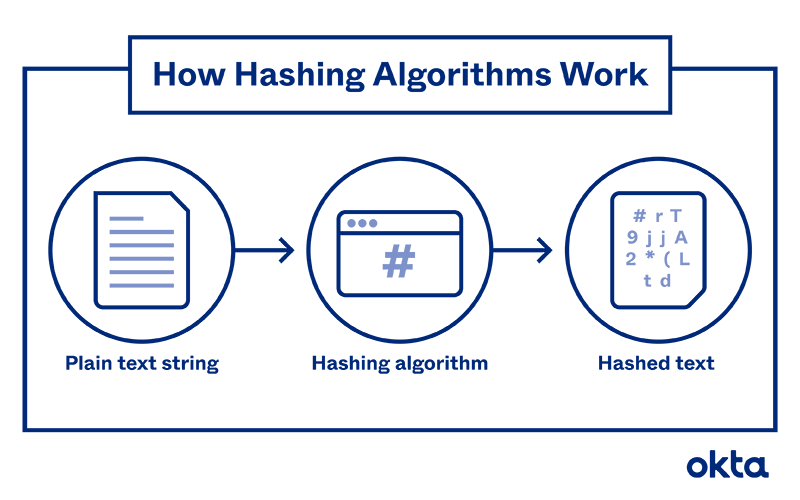
How does Hashing Work?
Hashing puts data through a hash function or algorithm to create an alphanumeric set of figures, or a digest, that means nothing to people who might view it. No matter how long the input is, the hash digest will be the same number of characters. Any minor change in the input, a misspelling, or upper case or lower case, will create a completely different hash digest. You can use the hash digest to confirm that the input exactly matches what is expected or required, for instance, a password. This is because, any change in the message will completely change the digest. Since the digest is different, it will indicate that someone corrupted the information by changing the message, and will not go through.
Hashing is an extra layer of defense. If you see a discrepancy, that means something has changed.
Reference
1. National Institute of Standards and Technology Glossary
Featured Image source: Okta.com
For a deep dive into hashing, check Okta’s Hashing Algorithm Overview: Types, Methodologies & Usage